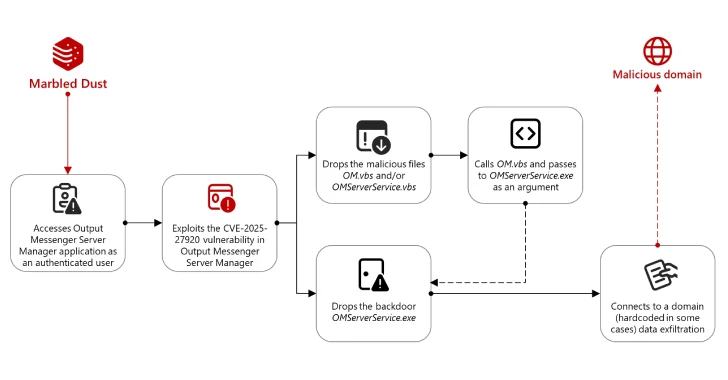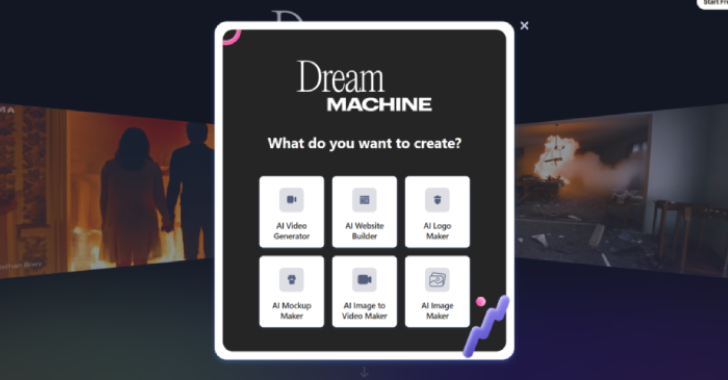
Overview
Threat actors are exploiting the growing interest in artificial intelligence (AI) by promoting fake AI-powered tools to distribute malware known as Noodlophile. This campaign has successfully targeted over 62,000 users through deceptive posts on social media platforms, particularly Facebook.